Affiliate links on Android Authority may earn us a commission. Learn more.
the Security Architecture of Android
Published onMarch 25, 2011
We all love Android. One of the major reasons we love it is the diversity of applications it provides us – the users. Undoubtedly, Android is a very versatile and customizable OS because of its many applications. But, have you ever wondered how your personal info is protected by this OS itself? Aren’t you eager to get an insight into the Security Architecture? If so, read on.

Let’s scrutinize the Android OS Security in a bit of depth. Android is a privilege-separated operating system. Each app runs through a unique Linux user ID. Linux helps in isolating applications from each other.
And, through additional permission mechanisms, restrictions are enforced on particular operations which may steal data from the device. Speaking in terms of layman language, the central architecture of Android security ensures that no application has permission to impact other applications, the operating system or the user (which includes the user’s private data such as contacts & e-mails). They also cannot access the network or keep the device awake without prior consent.
A very important anf compulsory file present in every Android App is “AndroidManifest.xml”. Let’s have a look at what this manifest file does (from the security point of view):
- It primarily describes the application’s activities, services and broadcast receivers.
- Some declarations in it let the Android OS know what components the app has and when there is a need to launch them.
- It declares which permissions the application needs for accessing the protected parts.
- It also declares the permissions that other apps require to have in order to interact with the application’s components.
The xml file in the app requires <user-permission> tags for making use of protected features on the device. When installing an application, the user is requested by the application package installer to grant permission(s). But, before or while running the application, it is never checked again by the user. If the permission was granted, the app can then use the desired features without prompting the user.

Moreover, another feature for all the .apk Android Applications is the signing of a certificate. The developer is identified by this signature and the private key is also held by him only. The purpose of this certificate is to distinguish the authors and allow the system to grant or deny signature-level permissions.
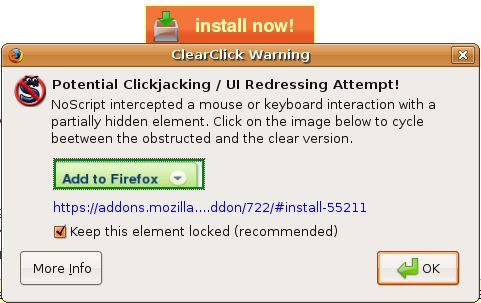
Thankfully, there have been significant security enhancements in the latest development of Android – Gingerbread 2.3. It’s said to prevent clickjacking attacks from cyber criminals. Clickjacking is basically an attack which tricks user into clicking rogue links disguised as legitimate page features. The Gingerbread platform is built with a touch filtering mechanism called “FilterTouchesWhenObscured” for the prevention from these types of attacks. This will alert users when their devices are obscuring or concealing sensitive functionality.
This was coders insight into the security design of our beloved Android OS. Now, it’s time to have a look at the loopholes friends! And, obviously in this competitive world, we are bound to compare the rivals. So, in our next post we will present the iOS Security design. And, we will also point out the gaps in Android OS by comparison.
Does your data feel secure on Android?
Also, image credit for the header image goes out to Norebbo. Check out his Android 3D work – it’s great!