Affiliate links on Android Authority may earn us a commission. Learn more.
Here's how Android 15 protects your two-factor authentication codes from malicious apps
Published onOctober 21, 2024

- Android 15 blocks untrusted apps from reading sensitive notifications, even if they have permission to read all notifications.
- Before Android 15, apps with notification access were able to read all incoming notifications, even ones with OTP codes.
- Now, though, only certain trusted apps can read OTP codes from notifications.
Your phone’s notifications panel is a treasure trove of sensitive data, as it includes not just personal messages but also security codes sent from online services you’ve enabled two-factor authentication for. That’s why many malicious apps try to trick you into granting them notification access so they can steal those two-factor authentication codes. Thankfully, the Android 15 update makes it harder for malicious apps to extract two-factor authentication codes from notifications.
Android has long offered an API called Notification Listener that lets third-party apps access your notifications. Since notifications can contain sensitive data, apps can’t use the Notification Listener API unless they get your permission. You have to manually grant the app access to your notifications through the Settings app, and the only thing apps can do to assist with that process is to open the Settings page where you can grant access.
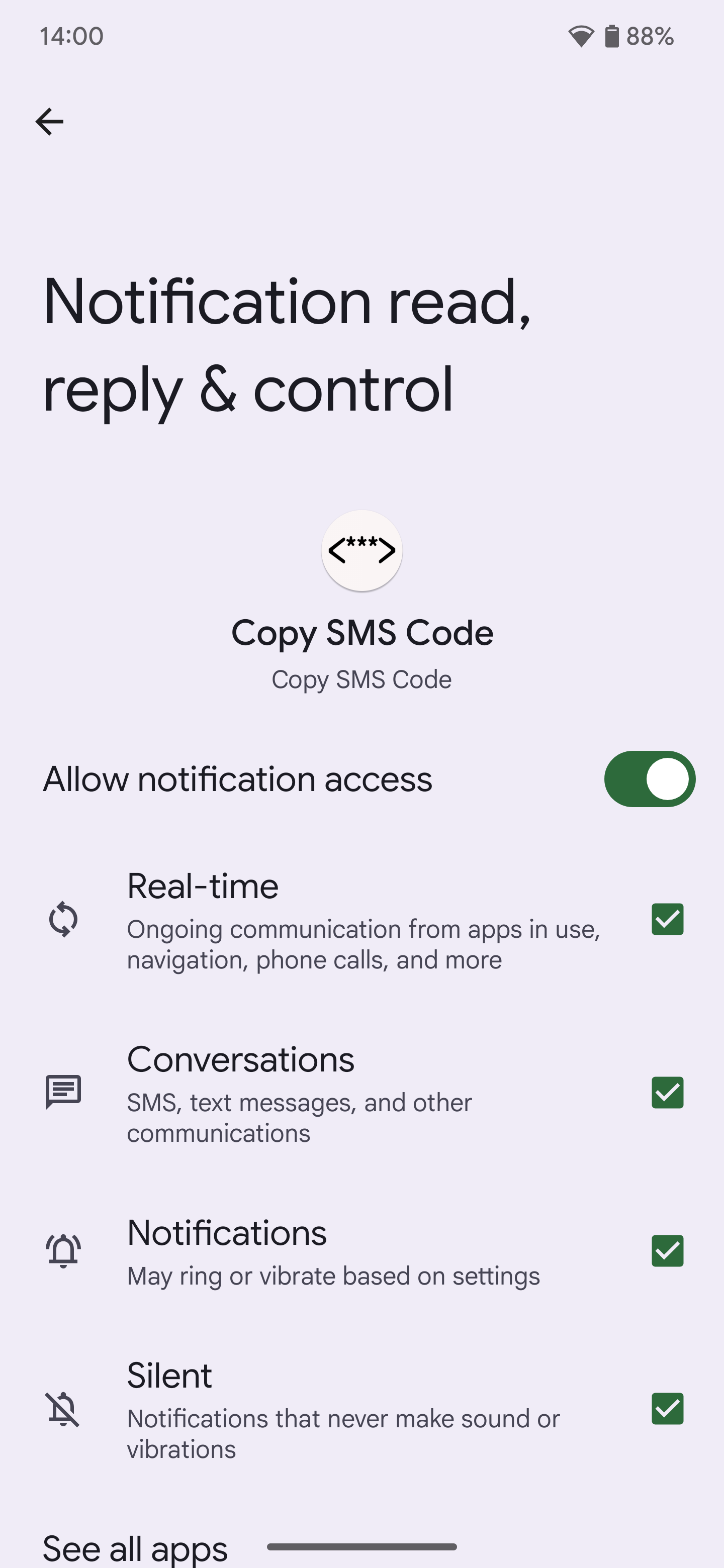
Once an app has been granted notification access, it can read, reply to, dismiss, or control either all of your phone’s notifications or the subset of notifications that you gave it access to. It doesn’t matter if that notification includes something really sensitive like a two-factor authentication code — with the Notification Listener API, apps can read them and thus extract them.
Android 15 changes things by designating notifications with two-factor authentication codes as “sensitive” and only allowing “trusted” Notification Listener services to read them. Any “untrusted” Notification Listener service that tries to read notifications with two-factor authentication codes will simply be given a message stating, “sensitive notification content hidden.”
Here’s a short video demonstrating how this change affects Notification Listeners on Android 14 versus Android 15. In this video, you can see that an app that I’ve granted notification access to on a device running Android 14 can read notifications with two-factor authentication codes in them. In contrast, the same app with the same permission on a device running Android 15 cannot read notifications with two-factor authentication codes in them.
Under the hood, the Android System Intelligence (ASI) app processes all notifications before they’re sent to Notification Listener services. If ASI detects that a notification has a two-factor authentication code in it, it’ll tell the system to mark it “sensitive” and block it from being sent to “untrusted” Notification Listener services. “Untrusted” Notification Listener services belong to apps that don’t hold the new RECEIVE_SENSITIVE_NOTIFICATIONS permission that Google has added in Android 15.
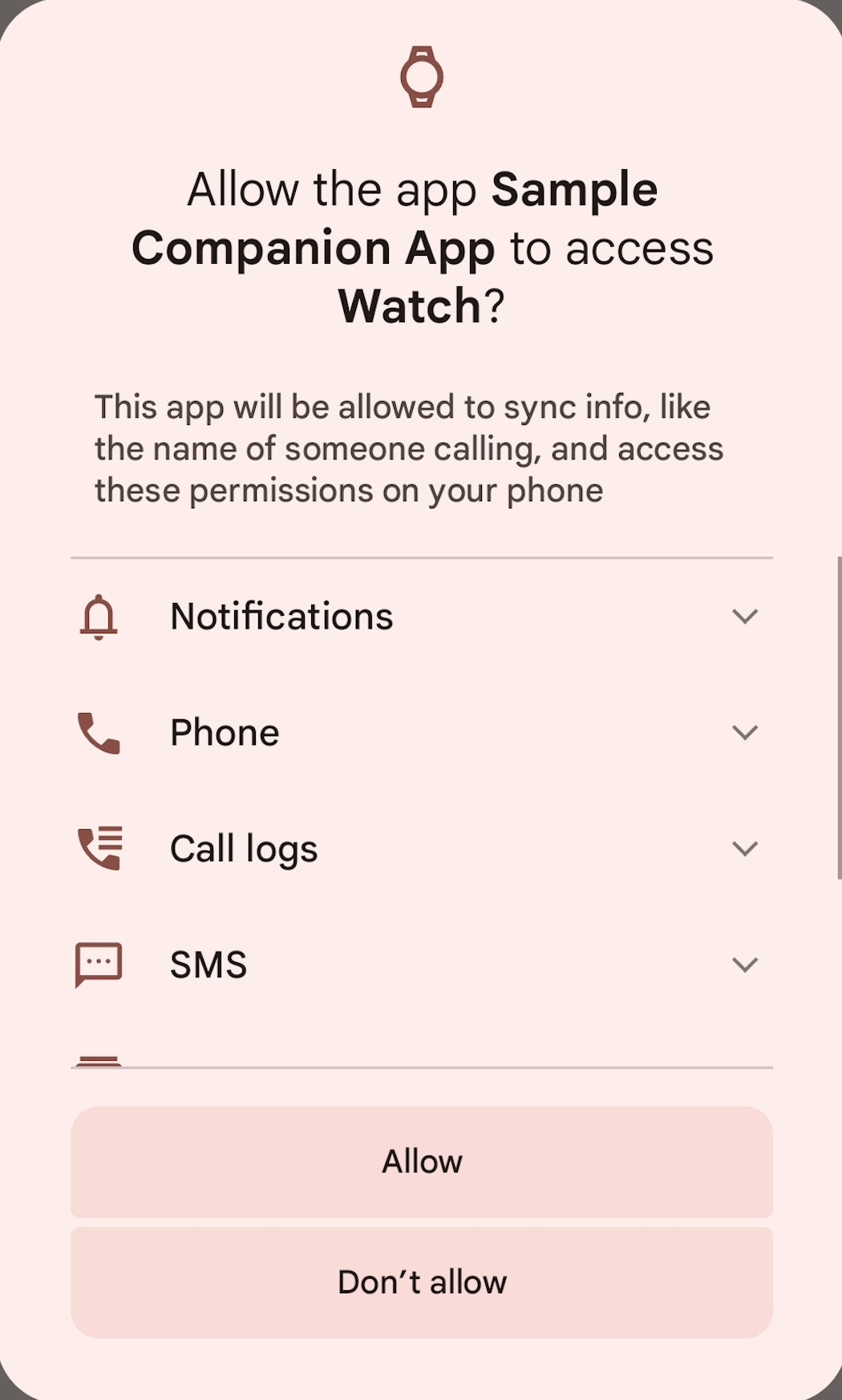
This permission can only be granted to apps signed with the system certificate or to apps that hold certain roles. Most of the roles that are granted the RECEIVE_SENSITIVE_NOTIFICATIONS permission can only be held by system apps, but there are some that can be held by third-party apps, too, like COMPANION_DEVICE_WATCH, COMPANION_DEVICE_GLASSES, and HOME. Respectively, these roles are given to watch companion apps, smart glasses companion apps, and the default launcher. In other words, the only third-party apps that can read notifications with two-factor authentication codes in them on Android 15 are apps that connect to your smartwatch, apps that connect to your smart glasses, or your default home screen launcher app.
Blocking third-party apps from reading notifications with two-factor authentication codes in them will hopefully stop some hacking attempts, but it’ll also break some automation and convenience tools such as “Copy SMS Code,” the free and open source app I used to demonstrate these changes. There is an easy workaround to restore the old behavior, but it’s not something I recommend. It involves turning off “Enhanced notifications” under Settings > Notifications. This stops ASI from parsing notifications and marking ones with two-factor authentication codes as “sensitive,” but it also stops it from generating suggested actions or replies. Another workaround requires setting up and using ADB to manually grant the RECEIVE_SENSITIVE_NOTIFICATIONS permission using the following command:
adb shell cmd appops set --user 0 <PACKAGE> RECEIVE_SENSITIVE_NOTIFICATIONS allowHere, <PACKAGE> is the package name for the application you want to grant the permission to. You should only do this if you’re a power user and there’s some tool this change otherwise breaks, though.
It’s great to see Android make tiny tweaks like this that improve security, but it would be nice if Google documented this change somewhere, especially because it impacts app behavior. It would also be nice if Android selectively blocked sensitive notifications from appearing on the lock screen, which is something Google was testing when I first reported on this change back in February — maybe that one will arrive in a future Android update.