Affiliate links on Android Authority may earn us a commission. Learn more.
January security update patches Factory Reset Protection bypass bug
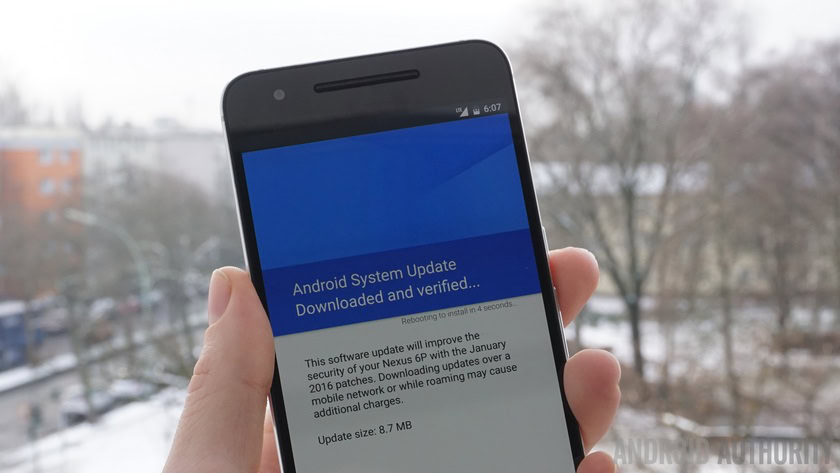
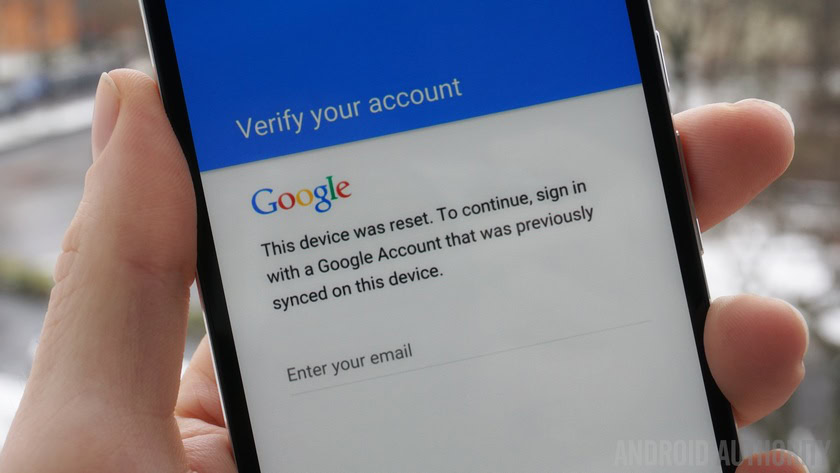
The latest Android security update seems to be holding true to its promise – patching a Factory Reset Protection (FRP) bypass bug that had recently been publicized. The bug allowed you (or a thief) to factory reset a Nexus device without requiring the credentials of the Google account previously associated with the device to reboot it again afterward.
Even though the bypass was a bit obscure, it’s good to see that Google is actively tackling any and all security weaknesses it comes across in a prompt fashion. The same FRP bypass bug was also recently exposed for Samsung devices and was previously uncovered for LG devices late last year. The Nexus vulnerability was only just shared on Reddit, after the bug had already been fixed.
The device discussed in the video shared on Reddit was still running the December security patch. The Android team clearly outlined the bug fix in the Nexus Security Bulletin (yes, there is such a thing) for the January patch:
An elevation of privilege vulnerability in the Setup Wizard could enable an attacker with physical access to the device to gain access to device settings and perform a manual device reset. This issue is rated as Moderate severity because it could be used to improperly work around the factory reset protection.
As always, the moral of the story is to keep your device updated with the latest security patch and not to believe every scary Android security story you read. Chase the source, double check the facts and only then decide if you should start freaking out. In this case, you can carry on about your day.
Do you have the January security patch yet? Did you know this bug existed?