Affiliate links on Android Authority may earn us a commission. Learn more.
Chrome is finally closing an ancient browser loophole
Published onAugust 8, 2024

- Confusion over how to handle requests for 0.0.0.0 has exposed a security vulnerability in multiple browsers.
- Attackers could use this method to bypass Private Network Access protection.
- Google’s got a fix for Chrome that’s rolling out over the next few releases.
Zero’s a funny number, and one that’s been causing problems for computers ever since the first time someone tried to divide by zero. When we’re using numbers to express specific things, the idea of “nothing” also being a valid option isn’t always intuitive to handle. Today we’re looking at what can happen when some zeroes are interpreted by software in a way users weren’t expecting, and how threat actors are able to use that mishandling to their advantage.
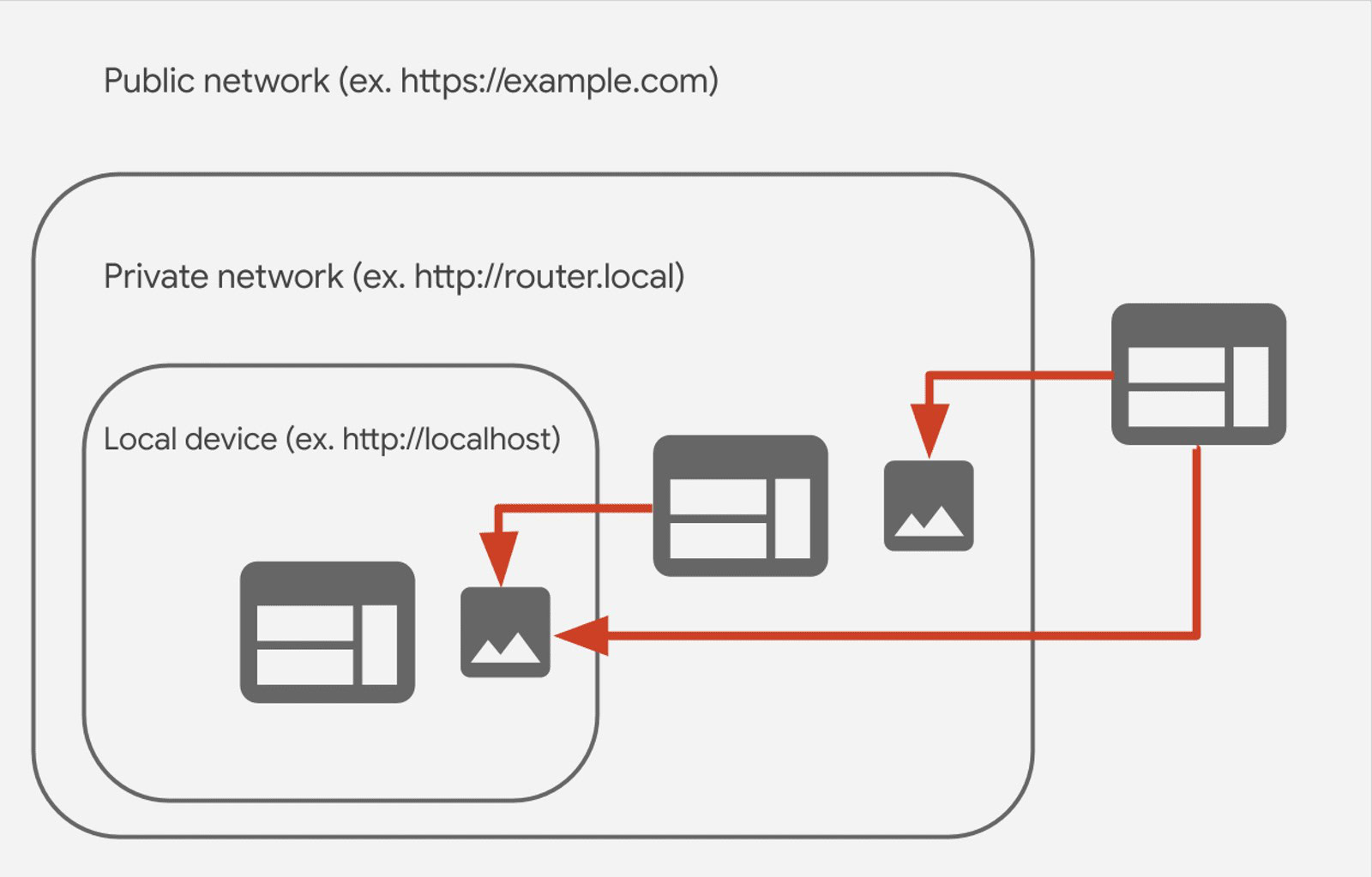
Our focus is on IP addresses (and the old IPv4, specifically), which uniquely identify every system on a network through a set of four numbers. As you may be aware, some of these numbers have special properties, like the IP address 127.0.0.1, which is known as localhost and serves as a loopback — basically, it’s like holding up a mirror to a device on a network, and no matter who you are, when you try to connect to 127.0.0.1, you’re just trying to connect back to your own device. This sort of behavior is pretty much standard everywhere, and software knows how to handle it.
This all leads us to: 0.0.0.0. If that IP address looks weird to your eyes, imagine what it looks like to a computer. The big problem with 0.0.0.0 is that there’s not a strong consensus on how systems should treat it. Some don’t see it as a valid address at all, while others handle it just like a 127.0.0.1 loopback. And rising from that confusion, hackers have found a way to abuse 0.0.0.0, as uncovered by Oligo Security (via Forbes).
Even if you’re not personally hosting a web server, lots of software makes itself available over your local network — like how you might use your browser to connect to and configure your router. Stuff like that is largely meant to be kept separate from the internet at large, and Chrome offers a system of protection called Private Network Access (PNA) to keep it that way. For instance, an attacker might prepare a web page that instructs your browser to make requests to that loopback address, or other address on your local, internal network, where software like this is running. Unchecked, that could result in you unintentionally exposing private data. But thanks to PNA, Chrome knows to keep these two local and remote worlds separate.
Problem is, no one really thought about 0.0.0.0 when building any of this. And so, a lot of the time, hackers can just use 0.0.0.0 to bypass those PNA protections. Maybe the worst part? This has been the case for at least 18 years now.
Apple and Google are fixing their browsers to close this hole, but Mozilla’s not quite convinced when it comes to Firefox. Basically, the team’s concerned that if devs have been treating 0.0.0.0 as loopback for years, suddenly changing that could threaten to break a lot of software. While the plan is to block 0.0.0.0 eventually, if you’re concerned about this attack vector you may want to consider another browser for the time being.