Affiliate links on Android Authority may earn us a commission. Learn more.
Google bans 13 apps that secretly download other malware
Published onJanuary 8, 2016

The Google Play Store can be a sketchy place, with less-than-honest app developers sneaking all manner of corrupt and malicious content into the Android market place. Occasionally even very popular apps get unmasked as malware, like 13 that have just been banned by Google, in the process revealing it was the malware itself that made them so popular.

The whole thing works like an organized crime ring. Fully functioning apps that seem, on the surface, to be innocuous secretly download other apps in the scam ring, artificially boosting their download numbers. Some even have the ability to leave positive reviews and ratings without the owner’s knowledge. As each new app is installed the cycle begins again.
Others seek root privileges (without the owner knowing) with the intent of surviving a factory reset if the victim ever suspects something is amiss. As the Lookout Security researcher that uncovered the scam notes: “Specifically, it attempts to detect if a device is rooted, and if so, copies several files to the /system partition in an effort to ensure persistence, even after a complete factory reset.”
Sadly, this kind of underhanded approach isn’t even new, with several other “malware families” recently using a similar tactic. The scary part of these app families, known as Shedun, Shuanet and Shiftybug, is that they could auto-root a device in order to install themselves on the system partition. The only upshot is that these apps were found in third-party Android market places, not Google Play.

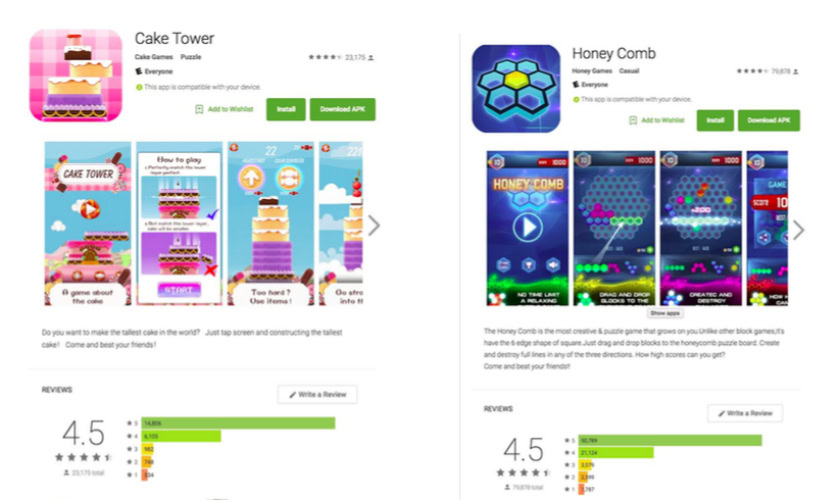
By contrast, the apps that have just been uncovered have managed to sneak the same malicious code into the Play Store itself, making them that much more sophisticated and dangerous. A part of the Brain Test family, these 13 apps had been installed on millions of devices and had excellent user reviews. As mentioned above though, these figures were manufactured by the malware itself.
If you’ve installed any of the following apps you might be affected, but Lookout assures users of its app that they are protected. Unfortunately, there isn’t a simple solution for removing the threat either. If the apps have gained root access, uninstalling them through the Android system or Play Store, or even factory resetting your device, might not have any impact.
- Cake Blast
- Jump Planet
- Honey Comb
- Crazy Block
- Crazy Jelly
- Tiny Puzzle
- Ninja Hook
- Piggy Jump
- Just Fire
- Eat Bubble
- Hit Planet
- Cake Tower
- Drag Box
The only real solution is to install a root explorer and go fishing for any suspect files, but even then you’ll have to know what you’re looking for. The only sure-fire way to remove the threat is to re-flash a manufacturer ROM, a process beyond the reach of some Android users. There are plenty of guides on the process for individual devices, but if you’re at all concerned, it’s probably best to contact your manufacturer for assistance.
Do you use an antivirus app? Have you ever been affected by malware?