Affiliate links on Android Authority may earn us a commission. Learn more.
Malicious Android adware campaign tries to exploit root access
Published onOctober 8, 2015

After the Stagefright fiasco I’m sure that the last thing you want to hear about right now are more Android security issues. But FireEye researchers have discovered an aggressive adware campaign, which they have dubbed Kemoge, that is targeting Android devices in more than 20 countries.
The malicious software is making its way onto Android phones and tablets by disguising itself as popular apps, with adware added in via repackaging. Once someone installs the infected software, the adware goes to work gathering up user data to sell and aggressively serving up irritating advertisements.

Kemoge apparently doesn’t stop there though, the apps then attempt to exploit eight common Android root methods in order to secure themselves deep into and to take over the system. It’s not clear how successful these exploits are, but if achieved, common processes such as com.facebook.qdservice.rp.provider are imitated to make adware removal much tougher and it even attempts to uninstall some antivirus software suites from devices.
Before anyone becomes too alarmed, the researchers note that these apps are being downloaded to users’ devices through third party app stores and web advertisement based installations. You’ve probably seen those pop-up ads that try and deceive customers into downloading software or claiming a free prize.
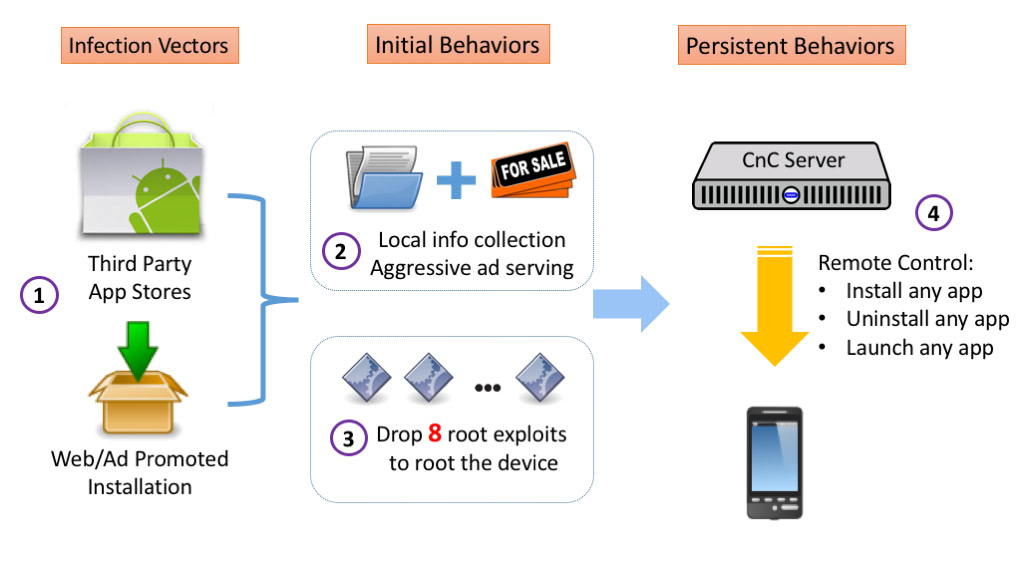
FireEye did spot one example of an app signed by the same developer certificate as an app from Google Play, but it didn’t contain any malicious code and has since been removed by Google. There’s no evidence to suggest that this adware campaign is affecting legitimate app services, so users who are careful about what they download should remain unaffected.
This is yet another reminder that legitimate stores are the safest place to download your Android apps. You can read the ins and outs about how the adware works in the source link below.