Affiliate links on Android Authority may earn us a commission. Learn more.
2FA hack reveals personal info on millions of people

- Users of the Twilio Authy Authenticator app may have had their phone number exposed to hackers.
- While the leak exposed personally identifiable information, it did not directly compromise accounts.
- Twilio has since secured its system, but warns the information exposed could be used for phishing.
Security is not something any of us get to ignore, and with so much of our lives tied to various accounts and services, protecting that access is critical. Users interested in making things as difficult as possible for hackers often look for login options that support two-factor authentication, preventing bad actors from messing with your data using a stolen password alone. Of course, that makes 2FA solutions themselves a prime target, and that’s just what Twilio has been dealing with recently, as an API vulnerability exposed some Authy user data.
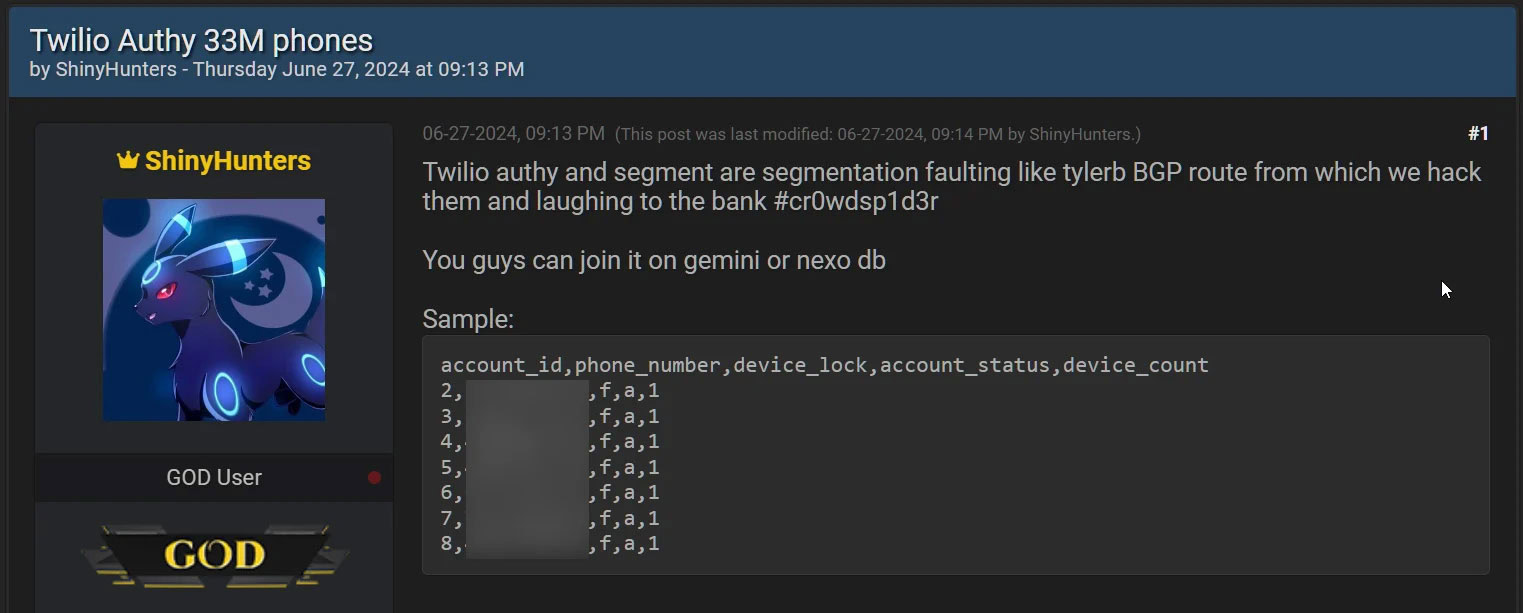
Authy is one of the more popular 2FA apps around, competing with the likes of Google’s own Authenticator. BleepingComputer reports that just about a week ago, hackers shared a data set consisting of some 33 million entries, connecting account IDs to user phone numbers. Twilio confirmed to the site that this data was scraped by way of a hacker connecting to a previously unsecured API endpoint — essentially, they could just run through a list of every possible phone number, and if one of them was associated with a registered Authy user, the API would respond with the linked account info.
To be clear, none of this exfiltrated data includes any passwords or anything that would directly provide access to your Authy account. But that said, your phone number is still very much personally identifiable information and could be combined with other data sets to become an increasingly useful (or, to you, threatening) profile for someone interested in compromising your security. As BleepingComputer notes, the references to “gemini” and “nexo” databases you see above are explicit instructions for this kind of cross-referencing.
Twilio has since shut down the exposed API that made this leak possible and advises updating Authy on your phone, but that sounds more like best practices than a specific fix for anything related to this attack.