Affiliate links on Android Authority may earn us a commission. Learn more.
How secure are password managers? Should you use one?
Published onJanuary 21, 2023
Most technology enthusiasts these days, including many of us here at Android Authority, swear by password managers. They’re often pitched as the easiest way to improve your online security, eliminating common problems such as easy-to-guess passwords and bad storage practices. Moreover, many even offer convenience through auto-fill as an added bonus. If you’re conscious about staying secure and private online, you’ve likely heard about password managers too.
The basic premise is simple: a password manager generates random passwords for each website or service you use. These passwords are then added to a virtual vault, locked behind a master password. This way, you aren’t expected to remember dozens of passwords — all you need is a single complex one. But how safe are password managers and does using one make you a vulnerable target?
Why use a password manager?

One of password managers’ greatest strength is their ability to generate complex passwords for you. Consider the following 18-character password, for instance, courtesy of my password manager: #*Si6Myx@BD2nqCAWa.
First and foremost, it’s completely random and unrelated to anything in my life, making it virtually impossible for anyone to guess through a social engineering attack. It doesn’t contain any common words or names either, so common dictionary attacks can be ruled out too.
Password managers generate random and unique passwords for each website, safeguarding you from future security breaches.
The randomness and uniqueness are equally important, especially if you tend to reuse passwords. Services like Have I Been Pwned will tell you exactly how many data breaches your email address has been associated with. If you use a password manager to generate dozens of uncorrelated passwords, your digital accounts are completely siloed from each other. Put simply, a single security breach at a random social media website won’t compromise all of your banking and sensitive accounts.
Related: 10 best security apps for Android
Are password managers safe? Can they get hacked?

Password managers sound complicated, but their security fundamentals are pretty simple to understand. In a nutshell, they rely on a specific cryptography technique called zero-knowledge encryption that ensures nobody except you can access your saved passwords. This is in addition to all of the usual online encryption practices, such as end-to-end encryption and encryption-at-rest.
Related: What is encryption?
The best way to understand the security model of a password manager is to look at cloud storage platforms like Google Drive or Dropbox. With these services, your data is encrypted, but the service provider themselves holds the authentication keys. Your password is only used to authenticate your account, not decrypt the actual data. Simply put, if the cloud provider’s servers were compromised along with the encryption keys, your data could be accessed remotely and without your knowledge.
It’s for this reason that no credible password manager service will ever record your master password or keep a copy of the encryption keys used to decrypt your vault. In other words, the application has “zero knowledge” of the encrypted passwords.
Password managers don't store a copy of the encryption key. In other words, nobody except you can access your vault.
We’ve seen a handful of high-profile password managers suffer security breaches in the past. However, to our knowledge none of them have leaked sensitive information like passwords or other vault content. Statistically speaking, using a password manager is far more secure than the alternative — writing down your passwords in a plain text document or reusing a predictable password across multiple sites.
The big downside to this iron-clad encryption technique is that you risk permanently losing access to your passwords if you forget the master password. You can’t simply contact customer support to “reset” your master password. In fact, that would imply the password manager can access your data at will — which is not very secure!
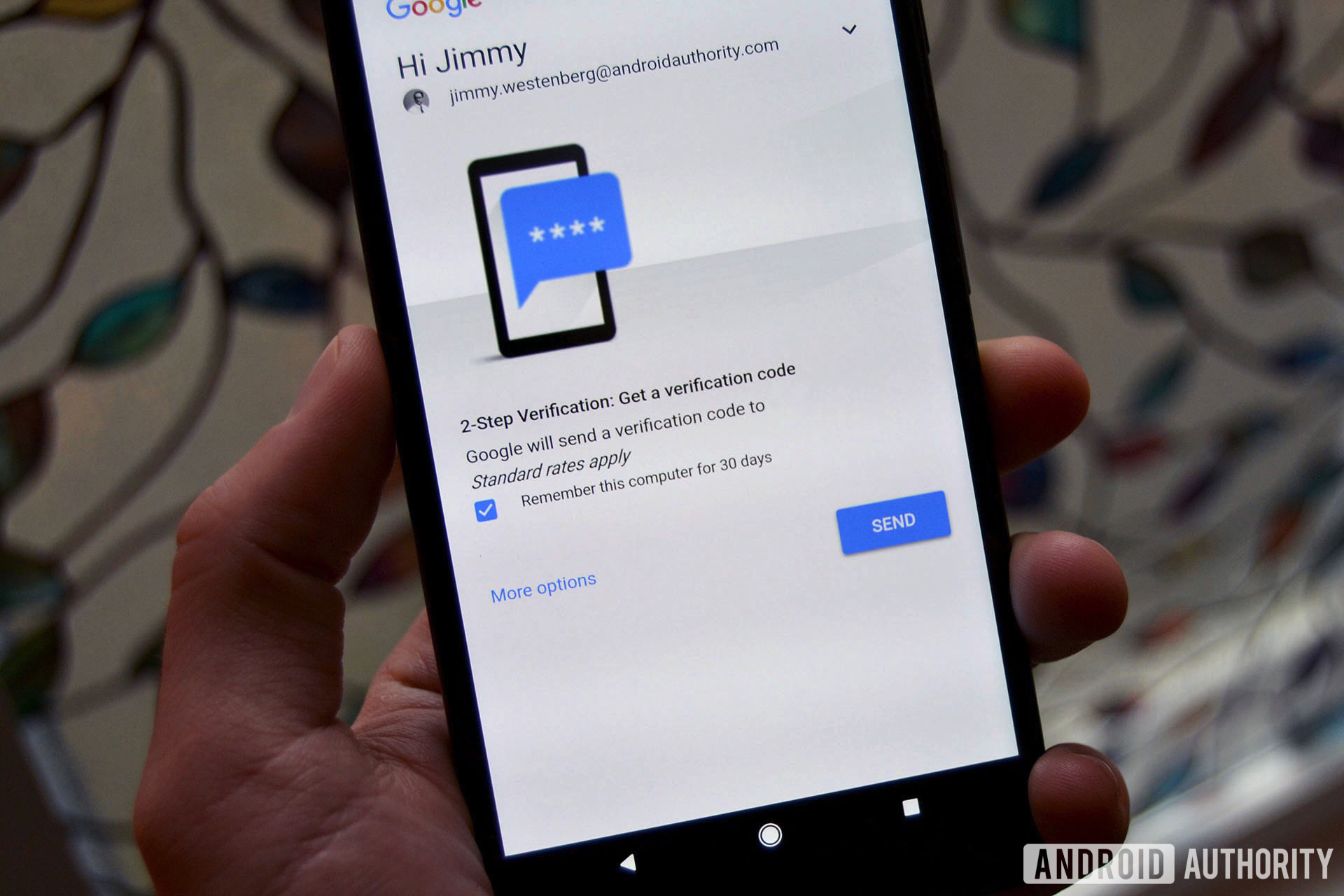
Use two-factor authentication for additional security
Of course, no software or technology is perfect. Password can be vulnerable in specific scenarios as well. However, these are almost always contrived scenarios that are unlikely to affect you.
Security researchers once uncovered a cache bug, for instance, that could have allowed an attacker to capture previously filled passwords. However, it required a specific series of actions on the user’s part — including visiting a malicious website. More importantly, though, the bug was fixed long before it was publicly disclosed, so its real-world impact was negligible, if not zero.
Popular password managers are regularly audited and security vulnerabilities are usually fixed before they become public knowledge.
The bigger vulnerability to consider is user error. Password managers themselves are quite secure, but the same cannot be said for the browser or other applications installed on your computer. A malicious program eavesdropping on your clipboard, for example, could easily siphon your passwords — and it wouldn’t be the password manager’s fault. Similarly, keyloggers could record your master password as you unlock your vault.
So how do you protect yourself against these hypothetical scenarios? Besides the obvious recommendation to download the latest security updates on all of your devices, you should consider using two-factor authentication (2FA). In fact, many password managers themselves can be secured with 2FA.
Put simply, two-factor authentication allows you to combine a password with something you have on your person. This can be via codes from an app like Google Authenticator or a dedicated hardware device, like a YubiKey. This way, even if an attacker gets their hands on your password(s), they won’t be able to access your accounts.
Finally, remember that you shouldn’t reuse your master password anywhere else. This can expose you to credential stuffing attacks, wherein attackers use stolen credentials to log into uncompromised services — like your password manager. We’ve seen a surge in credential stuffing attempts at major password management services of late.
Which password manager should you use?

With the basics out of the way, which password manager should you use? After all, there are dozens of options out there, with different feature sets and pricing to boot. Thankfully though, picking the most secure password manager isn’t very complicated. You can’t go wrong with any of the big names — at least from a security standpoint.
Most high-profile password managers are functionally identical, but can vary in terms of pricing, non-essential features, and other factors.
If you’re looking for an open-source password manager, Bitwarden is universally regarded as the best option. Basic functionality is provided for free, including unlimited cross-device sync. Even better, you can choose between Bitwarden’s cloud service or self-host your own installation on a local computer or server. The only downside to Bitwarden is that it’s a community-backed project, so there’s no guarantee of consistent updates.
If simplicity matters to you, LastPass and 1Password may seem more attractive. Both have existed for at least a decade and remain widely used today. They have premium tiers, but you may get extra features and potentially better customer support for your money.
See also: 1Password vs. LastPass
Finally, if cloud sync seems too risky, even with all the encryption and aforementioned best practices, KeePass is an open-source password manager that can secure your vault data in an offline database file. You’ll have to manually transfer the database to each device, and repeat the process each time you change the vault’s contents. You essentially trade convenience for increased security, for better or worse.
This is by no means an exhaustive list. You can find more password management tools, including Google and Samsung’s offerings, in our round-up of the best password managers for Android.