Affiliate links on Android Authority may earn us a commission. Learn more.
Apps can now better protect your data by making you close potentially risky apps
Published onSeptember 10, 2024

- The Google Play Integrity API has been updated with a new feature called app access risk.
- App access risk detects whether there are other apps running on the device that might be capturing the screen or controlling it.
- Developers can then prompt users to close these potentially risky apps before they can continue using their apps.
Every app developer is responsible for protecting their own users, but they have little control over what other software a user installs on their device — and for good reason. Users should be allowed to install whatever apps they want on their own personal devices (including via sideloading), but some of those apps could be malicious and do things like discreetly record the screen. That’s why Google is giving developers a new tool that forces users to close potentially risky apps before those apps can steal any data.
The new tool — called app access risk — is provided as part of the Google Play Integrity API. That’s the system that helps developers “check that interactions and server requests are coming from [their] genuine app binary running on a genuine Android device.” It analyzes the app that calls the API as well as the OS itself to look for signs of tampering. Apps that call the API receive an integrity verdict that tells them whether the app binary and the software environment it’s running in are “genuine,” i.e. they match versions that are known to Google.
Using the new app access risk feature, developers can determine whether there are other apps running on the device that might be potentially risky. These include apps that can capture the screen and apps that can control the device. Malware frequently abuses Android’s APIs for screen recording and accessibility control, which is why developers may want to be on the lookout for any active apps that have these permissions.
The way app access risk works is pretty simple. When developers call the Play Integrity API, they receive an integrity verdict that tells them whether there are any potential issues. If the environmentDetails.appAccessRiskVerdict.appsDetected field in the integrity verdict returns “UNKNOWN_CAPTURING,” “UNKNOWN_CONTROLLING,” “KNOWN_CAPTURING,” or “KNOWN_CONTROLLING,” then Google Play Protect has detected apps running that could be capturing the screen or controlling the device.
Developers can then show one of two remediation dialogs to prompt the user to close those apps. The CLOSE_UNKNOWN_ACCESS_RISK dialog should be shown if the developer wants the user to close apps that are unknown to Google — those that weren’t installed from the Play Store. The CLOSE_ALL_ACCESS_RISK dialog should be shown if the developer wants the user to close all apps capable of capturing the screen or controlling the device, even if those apps were installed from Google Play.
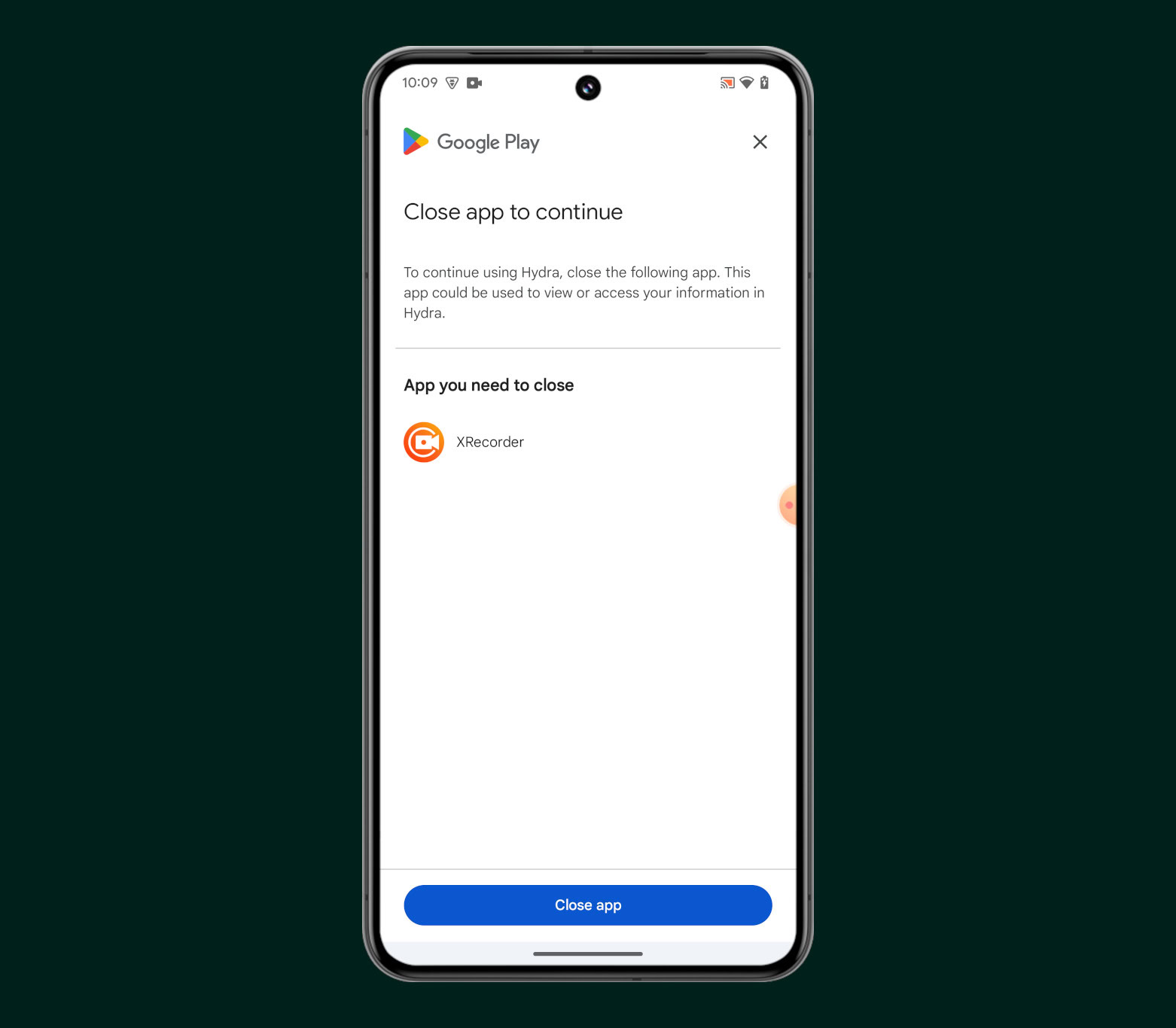
The only exceptions are genuine accessibility apps that are known to Google, i.e. apps on Google Play that formally declare they’re accessibility tools, which is only allowed for apps that undergo an extensive approval process. Genuine accessibility apps are excluded from the “KNOWN_CONTROLLING” response, so users who rely on them won’t be forced to disable them just to use other apps.
For privacy, developers who use the app access risk feature aren’t given any user or device identifiers, nor are they given any information about the apps that triggered the positive verdict. In other words, they’re only told that some apps are running that might be risky, but not what those apps are.
Google announced the app access risk feature at I/O earlier this year. It’s been available in public beta since then, with companies like NEWBANK, Revolut, Mercado Libre, and PhonePe already using it. The image I shared above is from an open source app made by developer linuxct to demonstrate the new functionality. Developers who are interested in the app access risk feature should check out linuxct’s demo app and Google’s documentation to learn more about how to implement it.