Affiliate links on Android Authority may earn us a commission. Learn more.
Rooted devices can expose your Google credentials, as proven by Samsung S-Memo database flaw
Published onNovember 13, 2012
Rooting your device has many benefits, including access to OS and firmware features that are otherwise inaccessible by regular apps. Rooting enables you to access hidden areas of the file system, control the CPU, tweak network settings, access Google Play from restricted devices, and more. But there’s also one thing that rooting enables: access to supposedly secure data.
The XDA Developers forum is known for its mobile development exploits, and community members usually publish their custom ROMs, tweaks and other tips. But a developer has noticed something that might be alarming to Android users in general. Rooting your device can potentially expose access credentials, which should otherwise have been hidden and inaccessible.
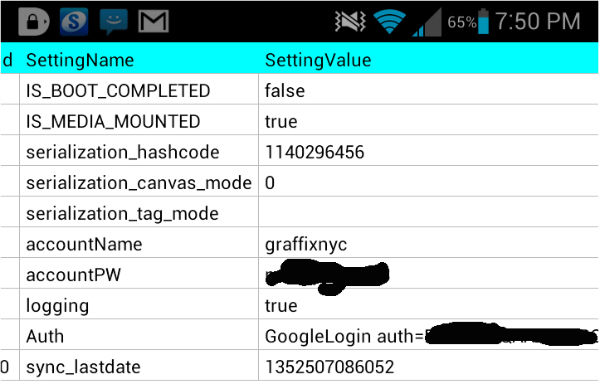
In particular, XDA forum moderator Graffixync says he was quite surprised to see his Google credentials stored in plain text in the Samsung S-Memo database.
I was poking around the S-memo databases when I opened a table using SQLIte editior. When I opened the table I was shocked to see my Google account username and password in clear plain text.
This may not necessarily hold true for all Android devices, as Graffixync says it’s likely a Jelly Bean specific issue. If you’d like to replicate the potential flaw, you can do if you have a rooted Samsung device, and if you have SQLite editor installed.
- Setup S-Memo to sync with your Google account
- Navigate to /data/data/com.sec.android.provider.smemo/databases using SQLite
- Open Pen_memo.db and look for the CommonSettings table.
If your device is affected with this potential vulnerability, then you should see your Google username and password in plain text.
Is this a flaw or is this normal with a rooted device?
Now the argument here is that with the act of rooting your device in the first place, your apps should have access to areas of the filesystem that are not otherwise accessible. As such, through rooting, the developer in this case was able to access the data through SQLite editor.
However, another argument here is that the username and password were stored in plain text and not encrypted. As such, any app that has access to root credentials would be able to retrieve this data. If the username and password were hashed, then it would be harmless even if an app could retrieve them. Is this a Samsung-specific flaw, then? Perhaps the developers of S-Memo forgot to ensure that user credentials would be encrypted.
Either way, this exploit illustrates the danger with rooting your device. For instance, side-loaded apps that ask for root permissions may potentially be retrieving user credentials from your app databases. Even apps from Google Play have the potential to do this if left unchecked.
Responsible Android device users should be more vigilant. Be careful what apps you give root permissions to.